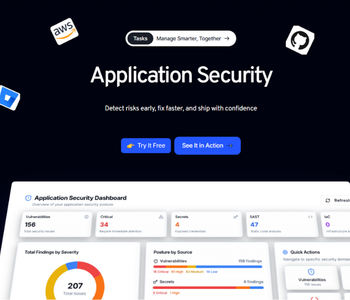
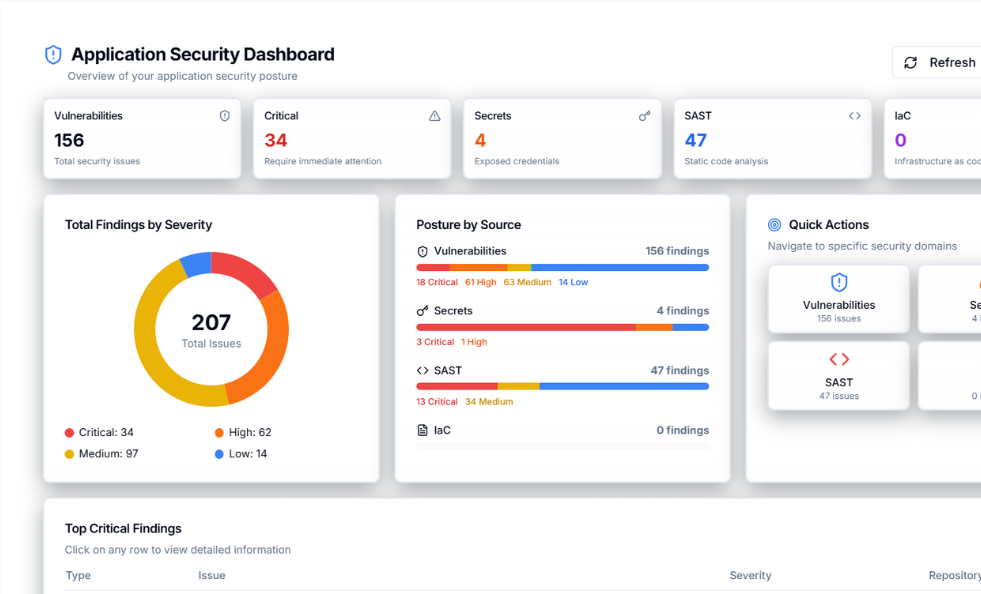
Application Security
Detect risks early, fix faster, and ship with confidence
ZERO-X
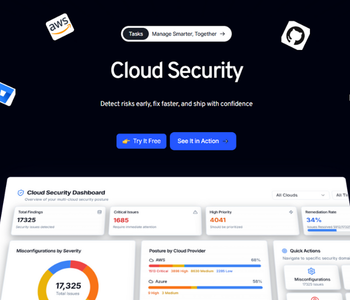
Unified Vulnerability Management
Find, prioritize, and fix risks across applications, APIs, and cloud dependencies from a single dashboard. Zero-X correlates CVEs with exploitability and reachability so teams focus on what truly matters.
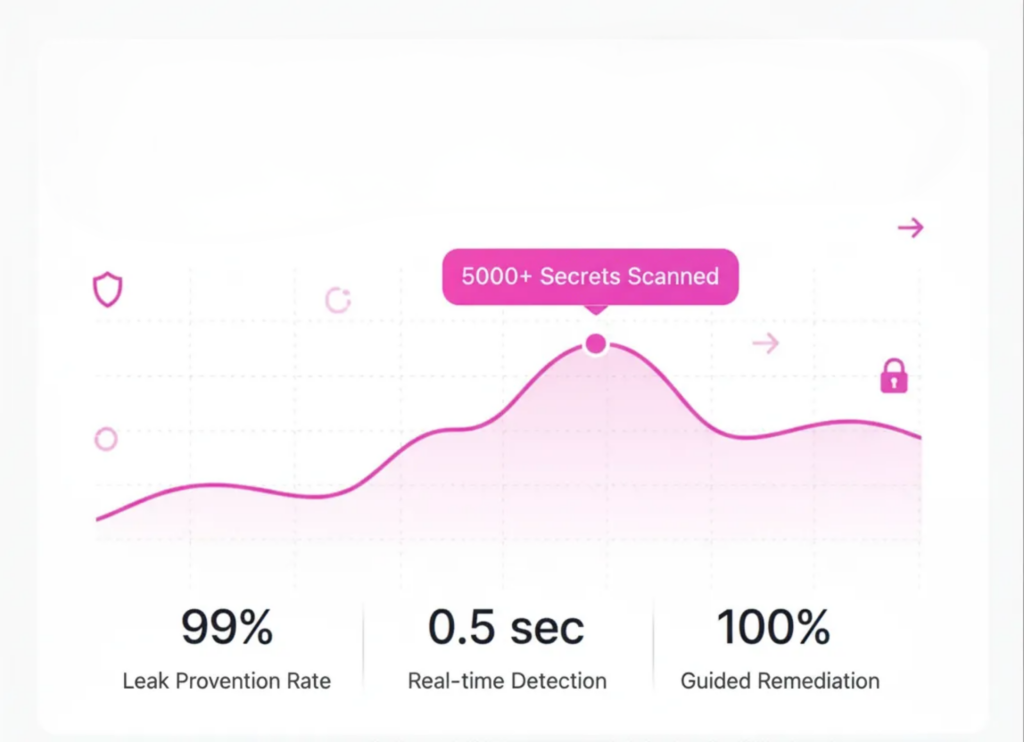
Secrets Detection & Leak Prevention
Automatically detect exposed API keys, tokens, and passwords across repositories, pipelines, and builds. Real-time alerts and guided remediation help prevent credential leaks before attackers exploit them.
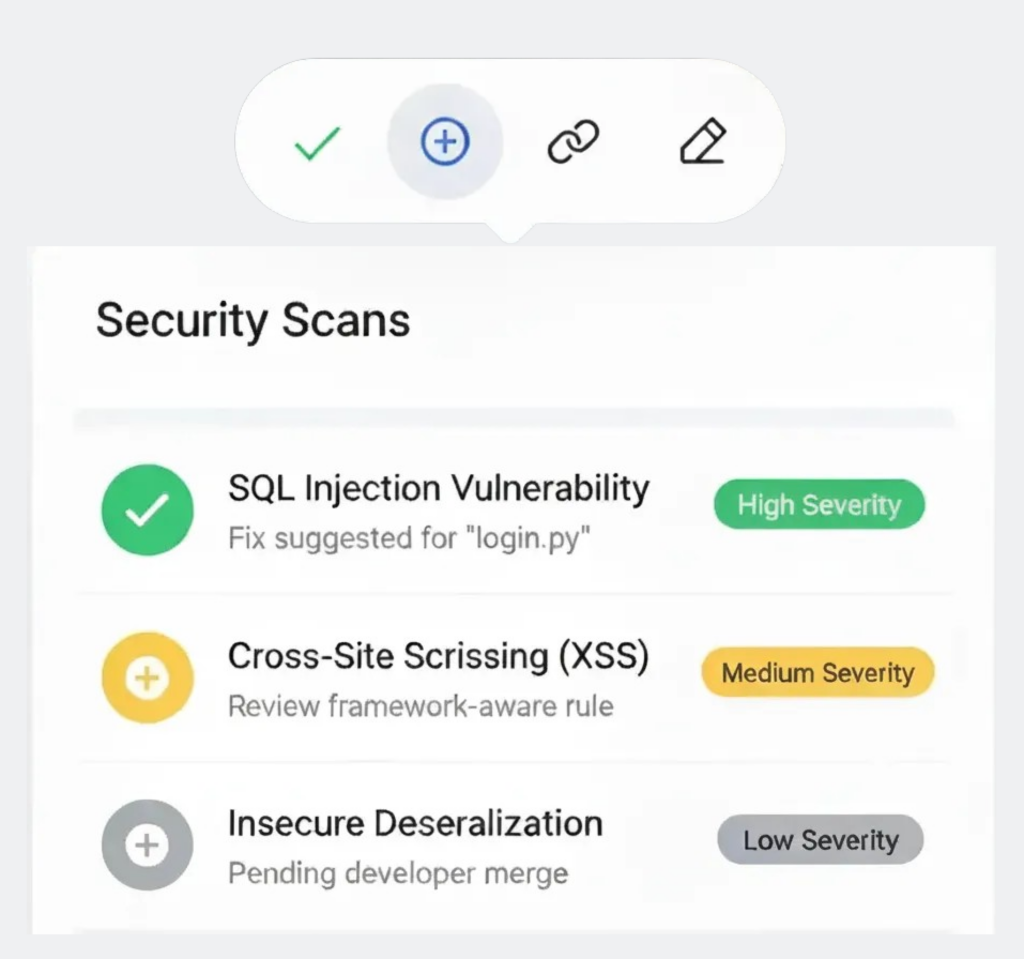
Static Application Security Testing (SAST)
Scan source code early in the SDLC to catch OWASP Top-10 vulnerabilities. Framework-aware rules and fix suggestions enable secure merges without slowing developers down.
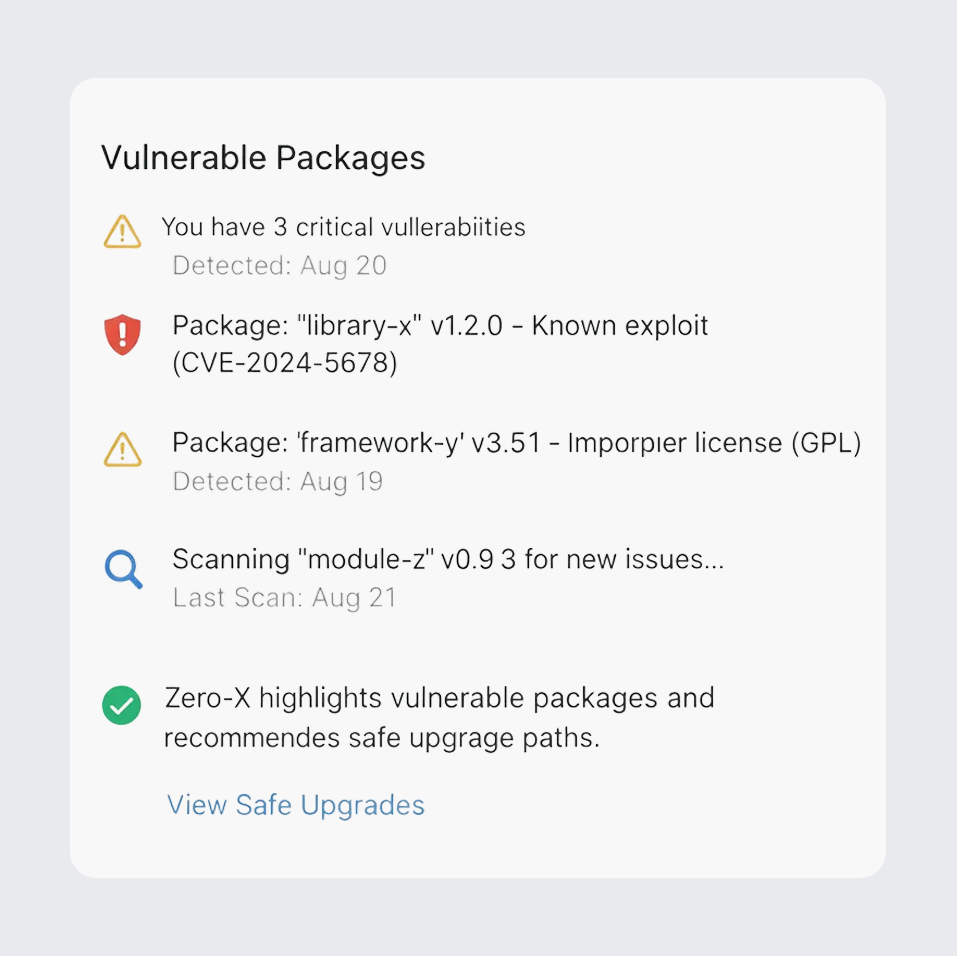
Dependency & Supply Chain Security
Gain deep visibility into open-source risks with SBOM generation, license guardrails, and dependency intelligence. Zero-X highlights vulnerable packages and recommends safe upgrade paths.
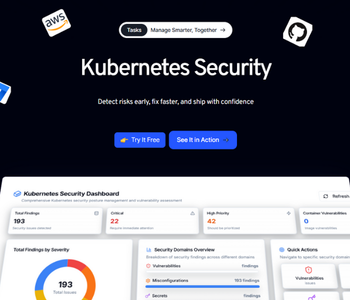
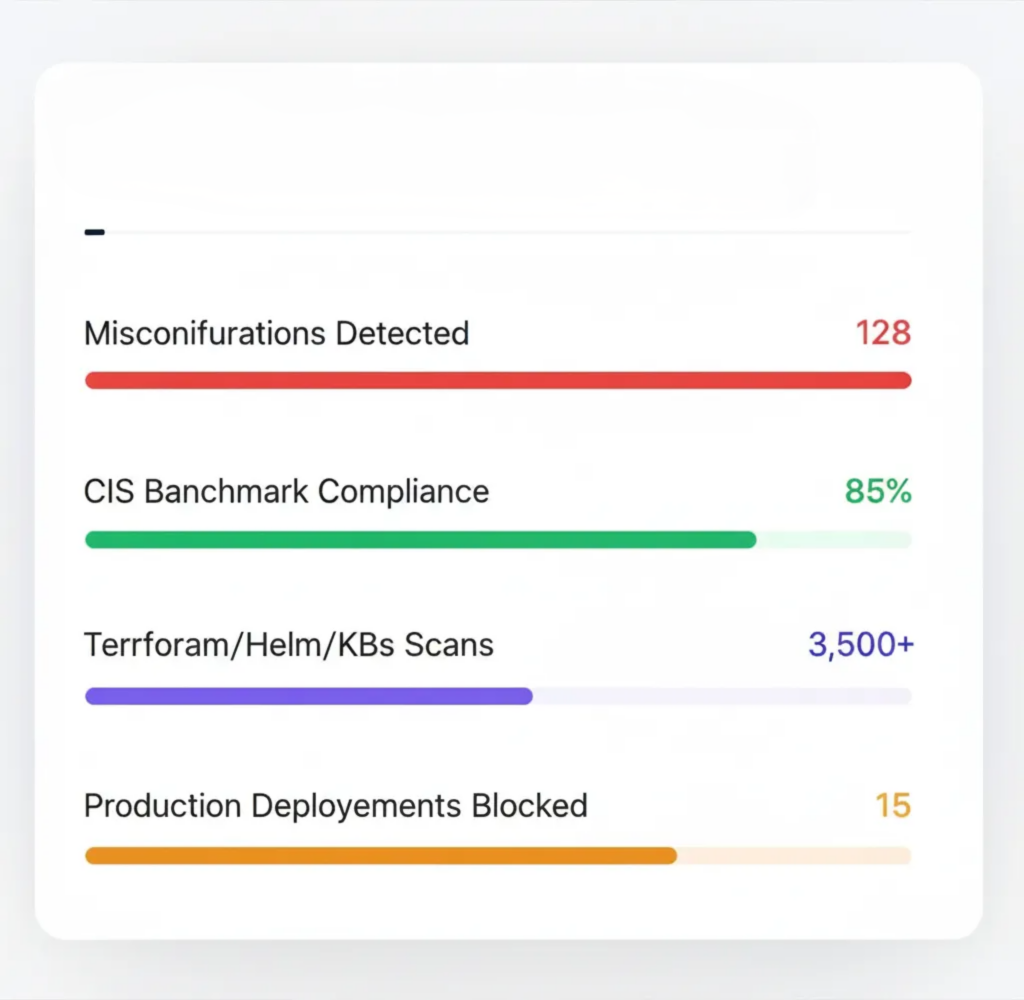
Infrastructure-as-Code (IaC) Security
Secure Terraform, Helm, and Kubernetes configurations with policy-as-code guardrails. Detect misconfigurations, map risks to CIS benchmarks, and prevent insecure infrastructure from reaching production.
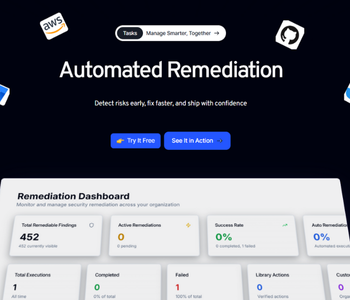
Beyond Code we detect, remediate, and secure your applications.
Vulnerability
Find and prioritize risks across apps, APIs, and cloud. Stay ahead with real-time CVE detection and fixes.
Your Dependency Risk Intelligence
✓ Real-time CVE detection with exploit signals and reachability hints
✓ Upgrade paths that name safe versions and suggest PR patches
✓ Policy gates in CI to stop risky builds before they ship
Open-Source License
✓ Automatic license ID (including edge cases) with allow/deny enforcement
✓ One-click reports for audits and third-party attestations
✓ Repo-level exceptions with expiry and reviewer workflow
SBOM & Provenance
✓ Per-build SBOMs you can sign and timestamp for traceability
✓ Component lineage across services, images, and environments
✓ Export in industry formats and share safely with customers and regulators
Secrets Detection
Find and prioritize risks across apps, APIs, and cloud. Stay ahead with real-time CVE detection and fixes.
Real-Time Secret Detection
✓ Monitor commits, PRs, branches, images, and pipelines as they happen
✓ High-signal patterns + entropy checks to cut false positives
✓ Instant alerts in Git, Slack/Teams, and CI
Broad Coverage, Zero Blind Spots
✓ API keys, OAuth tokens, DB passwords, cloud keys, certs
✓ Historic git sweep to catch long-lived leaks
✓ Custom detectors for internal token formats
SAST
Scan code early to catch OWASP Top-10 flaws. Enforce secure merges with framework-aware policies.
Static Code Analysis (SAST)
✓ Deep scan of source for vulns before build
✓ Detects injection, XSS, insecure deserialization, weak crypto
✓ Framework-aware rules with fix snippets
Sensitive Data in Code
✓ Finds hardcoded credentials, tokens, and PII
✓ Entropy + pattern logic to reduce false positives
✓ PR/MR annotations for instant developer action
Code Health & Maintainability
✓ Tracks complexity, duplication, and tech debt
✓ Enforces best-practice rules per repo/team
✓ Trend dashboards to spot risky modules early
IaC
Secure Terraform, Helm, and Kubernetes configs automatically. Stop risky defaults with policy-as-code guardrails.
IaC Configuration Analysis
✓ Flag risky defaults: public buckets, open security groups, weak encryption
✓ Map checks to CIS benchmarks and cloud best practices
✓ Surface blast radius and data exposure to prioritize fixes
Policy-as-Code Enforcement
✓ Write org rules once and enforce in CI/CD with merge and deploy gates
✓ Per-env exceptions with expiry, owner, and approval workflow
✓ Drift detection to keep runtime aligned with approved templates
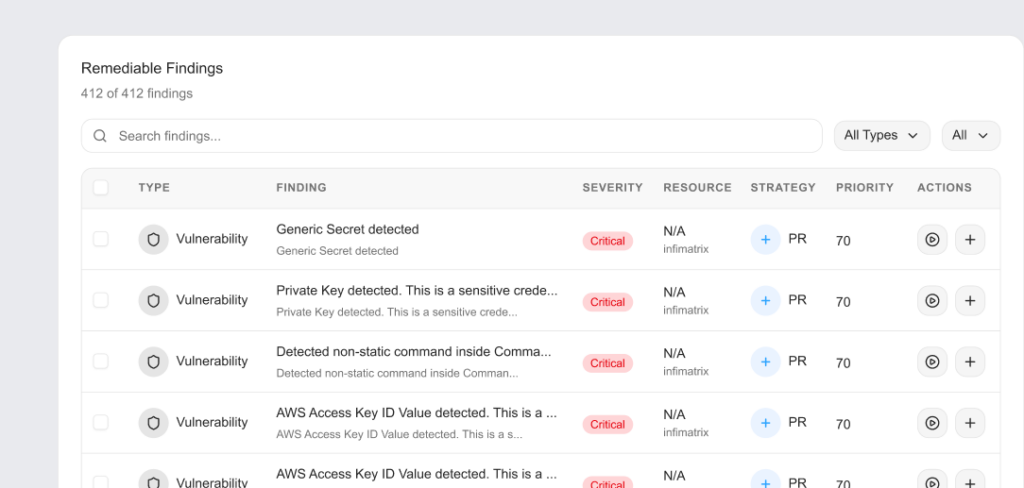
One Click Remediation
✓ One-click patches and ready-to-merge PRs for common misconfigs
✓ Inline fix hints with secure examples for each resource
✓ Rollback-safe changes with audit trails and SLAs








Connect What You Already Use
Zero-X seamlessly integrates with your existing cloud and development ecosystem AWS, GitHub, GitLab, Kubernetes, Docker, Google Cloud, Bitbucket, and more. Run security scans, enforce guardrails, track vulnerabilities, and automate remediation directly within your workflows.
1. What is Zero-X?
2. How quickly can I get started?
3. What integrations does Zero-X support?
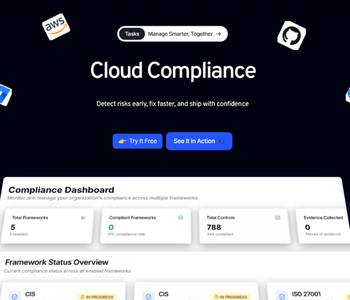
4. Does Zero-X help with compliance?
5. Can Zero-X fix vulnerabilities automatically?
Simple, Predictable Pricing
Choose the plan that’s right for your team. Start for free and scale as you grow. No credit card required. Signup for free.
Developer
For small projects and exploration.
Free
- 1 User
- 2 Data Source
- Upto 500 Resources
- Upto 5 Daily Scans
Pro
For teams in growing businesses
Billed Annually or Monthly
- 5 Users
- 10 Data Sources
- Upto 1000 Resources
- Upto 50 Daily Scans
Enterprise
For teams in enterprises with complex needs
Billed Annually
- Multiple users
- Unlimited Data Sources
- Multiple Resources
- Unlimited Scans
- SAML/SSO Integration