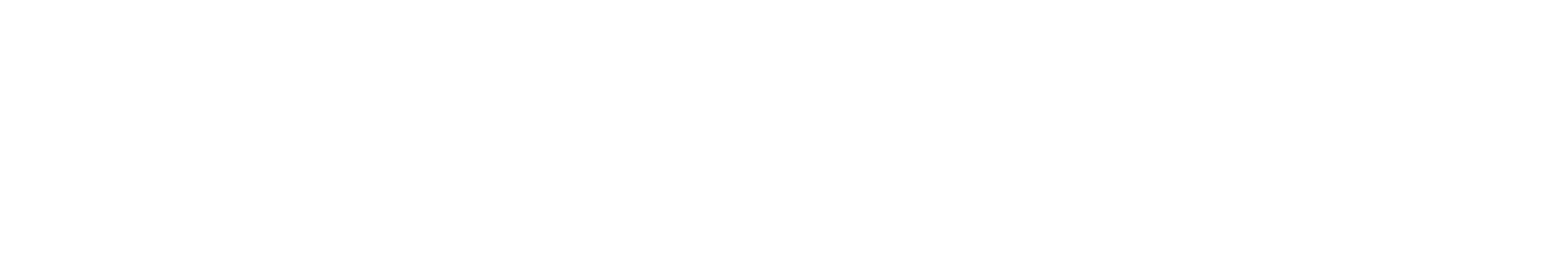Kubernetes Security
Detect risks early, fix faster, and ship with confidence
ZERO-X
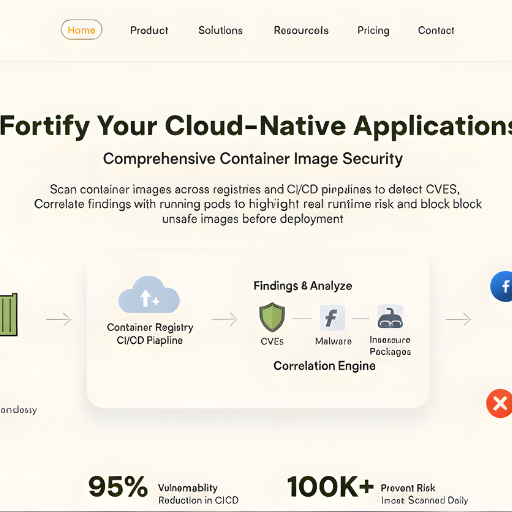
Container Image Security
Scan container images across registries and CI/CD pipelines to detect CVEs, malware, and insecure packages. Zero-X correlates findings with running pods to highlight real runtime risk and block unsafe images before deployment.
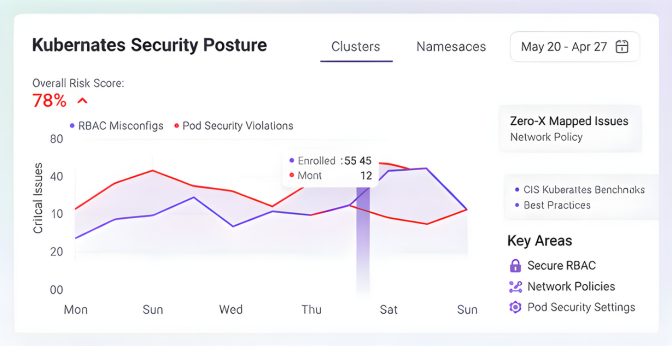
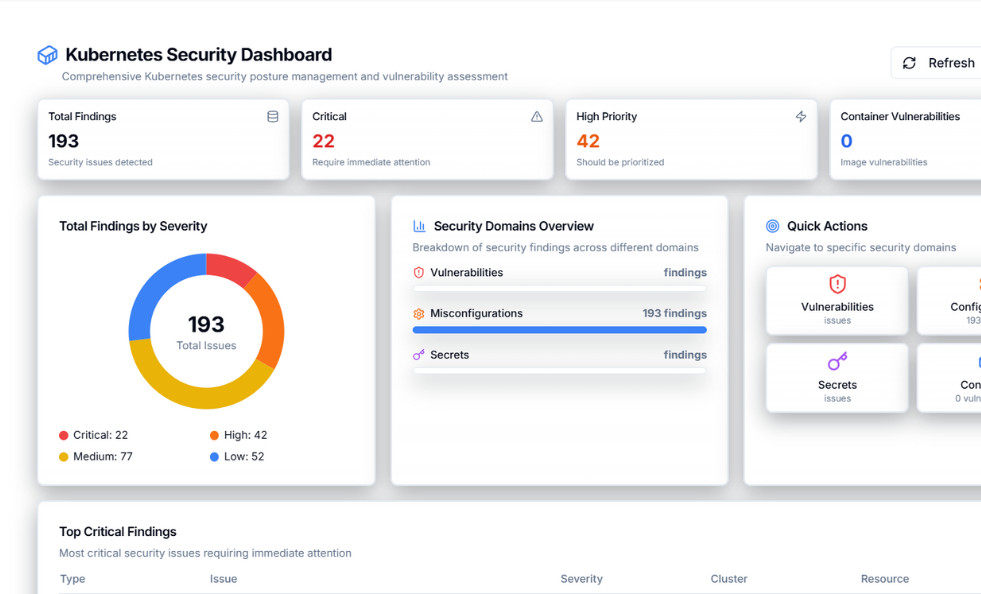
Kubernetes Configuration Hardening
Detect misconfigurations across clusters, namespaces, and workloads. Zero-X maps issues to CIS Kubernetes Benchmarks and best practices, helping teams secure RBAC, network policies, and pod security settings.
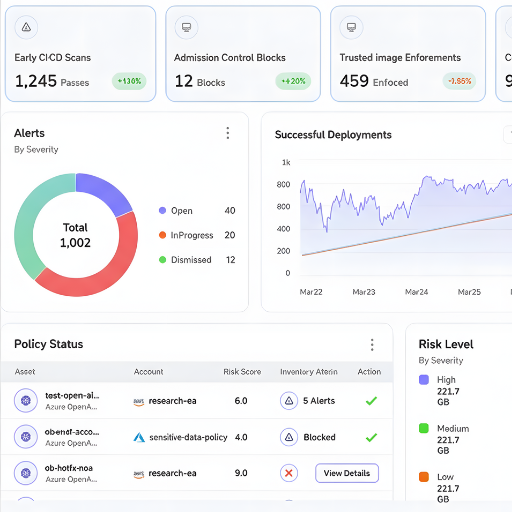
Secrets Security & Protection
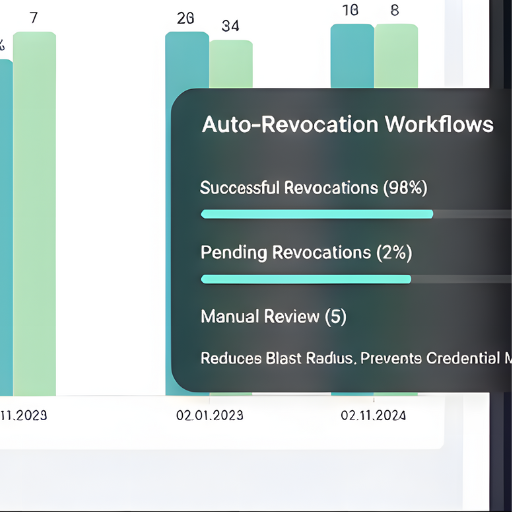
Identify exposed secrets such as API keys, tokens, and certificates in manifests, images, and pipelines. Continuous monitoring and auto-revocation workflows reduce blast radius and prevent credential misuse.
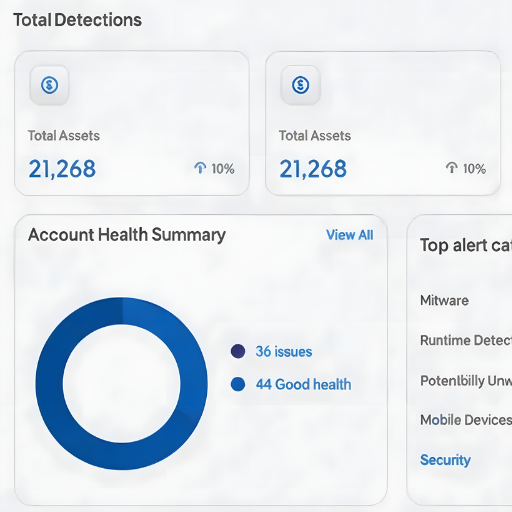
Runtime Risk Visibility
Gain real-time visibility into what’s running inside your clusters. Zero-X links vulnerabilities to active containers, services, and namespaces so teams can prioritize issues with actual exploit impact.
Policy Enforcement
Enforce Kubernetes security policies early in CI/CD and admission control. Block risky deployments, enforce trusted images, and maintain compliance without slowing developer velocity.
Beyond Code we detect, remediate, and secure your applications.
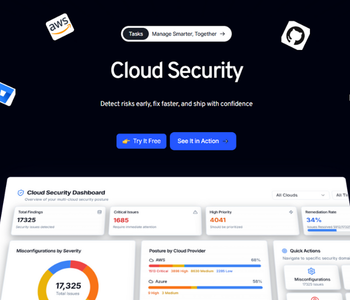
Kubernetes Security
Secure clusters end-to-end with image scanning, config hardening, and secrets protection
Container Image Security
✓ Container images are scanned to detect CVEs, malware, and misconfigurations.
✓ Vulnerabilities are correlated with running containers and namespaces for real impact.
✓ Risky images are blocked in CI/CD pipelines with enforced policy gates.
Configuration Security
✓ Detects insecure defaults and misconfigurations across cloud, Kubernetes, and IaC templates.
✓ Aligns resources with CIS benchmarks, industry best practices, and compliance frameworks.
✓ Prioritizes issues by severity, blast radius, and exposure for faster resolution.
Secrets Security
✓ Detects exposed API keys, tokens, passwords, and certificates across code, pipelines, and containers.
✓ Monitors commits, PRs, and histories in real time with high-accuracy pattern + entropy checks.
✓ Enables auto-revocation, rotation, and policy gates in CI/CD to prevent future leaks.








Connect What You Already Use
Zero-X seamlessly integrates with your existing cloud and development ecosystem AWS, GitHub, GitLab, Kubernetes, Docker, Google Cloud, Bitbucket, and more. Run security scans, enforce guardrails, track vulnerabilities, and automate remediation directly within your workflows.
1. What is Zero-X?
2. How quickly can I get started?
3. What integrations does Zero-X support?
4. Does Zero-X help with compliance?
5. Can Zero-X fix vulnerabilities automatically?
Simple, Predictable Pricing
Choose the plan that’s right for your team. Start for free and scale as you grow. No credit card required. Signup for free.
Developer
For small projects and exploration.
Free
- 1 User
- 2 Data Source
- Upto 500 Resources
- Upto 5 Daily Scans
Pro
For teams in growing businesses
Billed Annually or Monthly
- 5 Users
- 10 Data Sources
- Upto 1000 Resources
- Upto 50 Daily Scans
Enterprise
For teams in enterprises with complex needs
Billed Annually
- Multiple users
- Unlimited Data Sources
- Multiple Resources
- Unlimited Scans
- SAML/SSO Integration